In some situations, we need to check network connections, node configuration, dubug failures, problems or check something from the TKGs control plane or worker node. The case is, you can’t directly connect to this machine with a root or admin user. There are some steps, that you need to do, to achive this.
In this post, I want to show one way how to log in to the TKGs node.
Requirements:
- Running TKGs cluster (on vSphere 7 in this case);
- SSH access to the vCenter shell.
Before we start, remember to have a running TKGs vSphere namespace and cluster. I have vSphere namespace with a name ns01 and TKGs cluster with a name cluster01.

1. SSH to the vCenter
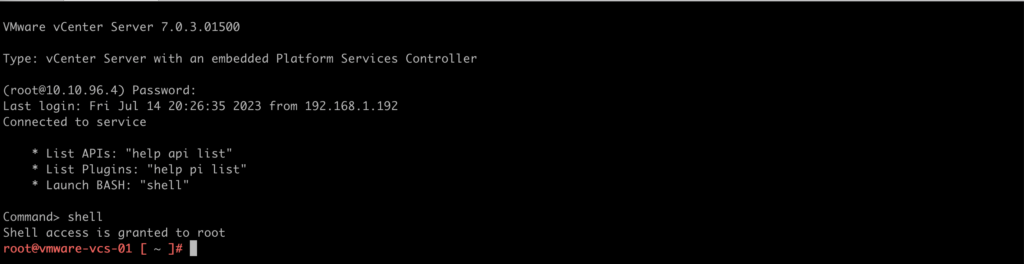
1. Log in to the vCenter shell using root user and IP/FQDN. Than, type shell command to get access to the operating system.
2. Access to the Supervisor cluster
1. At first, we need to gather an IP of the Supervisor cluster and password. For that, type a command:
/usr/lib/vmware-wcp/decryptK8Pwd.py
2. Than, using ssh and root user, access to the Supervisor cluster. Type ssh root@10.0.40.3 and provide PWD. And your’re in!

3. Access to the TKGs cluster
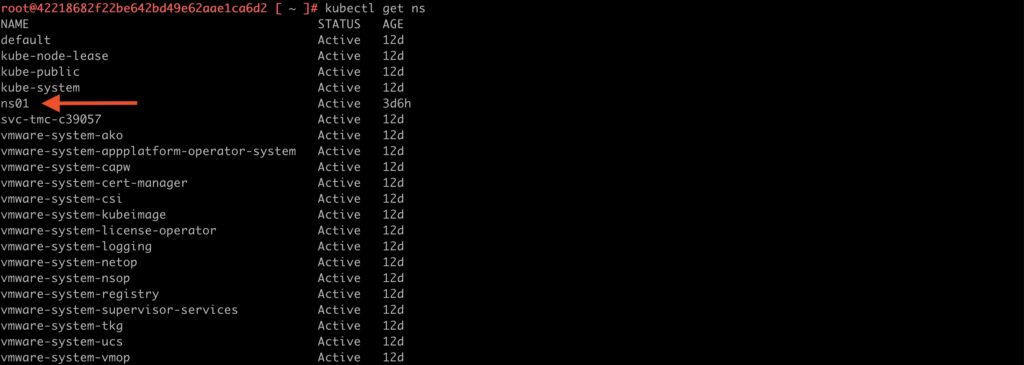
1. When we’re log in the Supervisor cluster, we can list all namespaces (and vSphere namespaces) existing on the Tanzu infrastructure.
Type: kubectl get ns
In this case, we are interested in vSphere namespace with a name “ns01“.
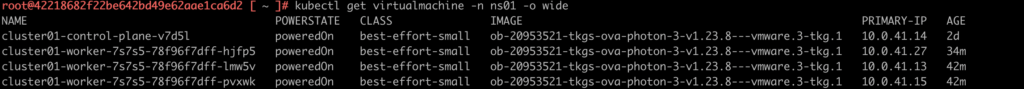
2. Optional step is to list TKG nodes (virtualmachine) with IP addresses running in this vSphere namespace.
To achieve that, type: kubectl get virtualmachine -n ns01 -o wide
You can check IPs for this node from vSphere interface too.
3. On each vSphere namespace, there are existing a few secretes. You can list it, with a command: kubectl get secrets -n ns01
In this case, we need to get information from cluster01-ssh-password secret.

4. Type a command kubectl get secrets -n ns01 cluster01-ssh-password -o yaml to get this secret with a YAML format. In the line “ssh-passwordkey” we have a password to this cluster. Now, we need to decode it and ssh to one of the four node.
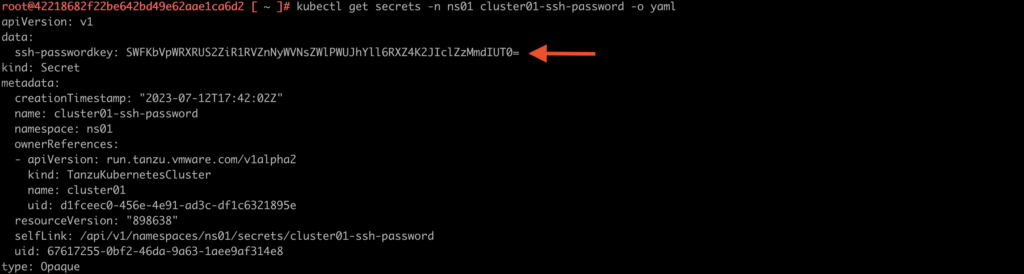
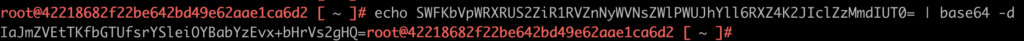
5. Decode password with a command:
echo SWFKbVpWRXRUS2ZiR1RVZnNyWVNsZWlPWUJhYll6RXZ4K2JIclZzMmdIUT0= | base64 -d
Now, we have a right password, which we can use to log in to the TKGs node.
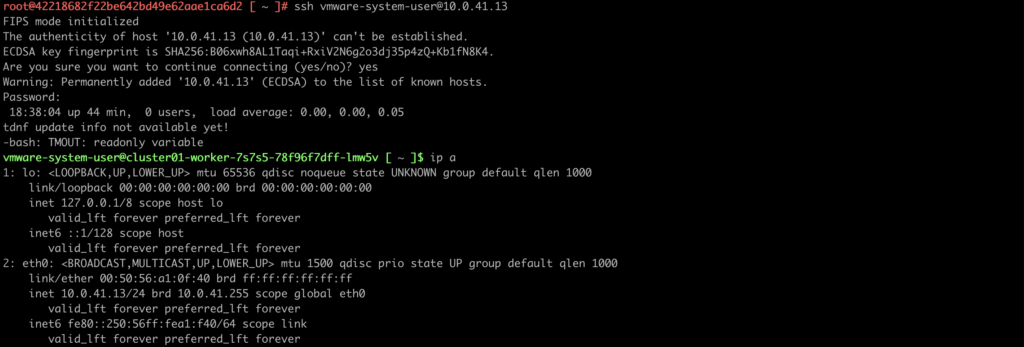
6. The last step is to ssh with a vmware-system-user account to the specific node. I use a worker node with a IP 10.0.41.13
Type a command: ssh vmware-system-user@10.0.41.13 and provide decoded password from the last step.
And finally, we’re logged in to the worker node!





































